Token permissions for GitHub Actions
GitHub Actions provide a default GITHUB_TOKEN that can be used by steps in your workflow that require access to your GitHub repository. However, some actions require more permissions than others.
Recently, the Test Reporter action in one of my workflows failed with the following error message:
Resource not accessible by integration
Although the message is not entirely clear, I quickly figured out that the problem was insufficient permissions. The action creates a check run and therefore requires write permission for checks.
Since the GITHUB_TOKEN permissions are listed in the log for the first step (Set up job) of each workflow run, I could easily confirm this:
GITHUB_TOKEN Permissions
Contents: read
Metadata: read
To fix the problem, I had to do a little more reading. As it turns out, GITHUB_TOKEN permissions can be configured at the repository, organization, or enterprise level. In my repository, they were obviously set to restricted read access. To change that, I had to navigate to my repository's Settings page, then select Actions and General in the left sidebar, and finally scroll to the bottom. There I was able to change the Workflow permissions to Read and write permissions:
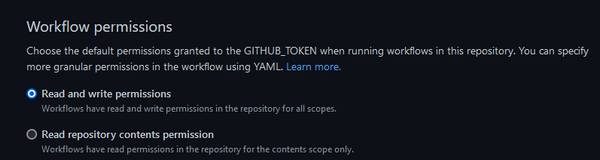
After running the same workflow again, the problematic action was now successful. I was also able to confirm from the log that the GITHUB_TOKEN used now had additional permissions:
GITHUB_TOKEN Permissions
Actions: write
Checks: write
Contents: write
Deployments: write
Discussions: write
Issues: write
Metadata: read
Packages: write
Pages: write
PullRequests: write
RepositoryProjects: write
SecurityEvents: write
Statuses: write
I still do not know why this new repository had read-only permissions set for the workflows. It was a personal repository and not part of an organization, so there is no way to set the defaults at a higher level. In another repository I created less than a month ago, the permissions were set to read and write. Perhaps the global default has changed since then.
This incident reminded me to pay more attention to the permissions granted to workflows. It makes sense to give workflows more restrictive permissions by default. As long as you are aware of this, it is very easy to grant them more permissions as needed. And if you need more granularity, you can always set permissions directly in the workflow file.
