Vulnerabilities in NuGet packages
The recently disclosed vulnerability in Newtonsoft.Json prompted me to take a closer look at the tools available in the .NET ecosystem for identifying referenced packages with known vulnerabilities.
If you primarily use Visual Studio 2022, you can check the referenced packages in your project or solution for security vulnerabilities in the NuGet Package Manager window. Any packages with known security vulnerabilities are marked with a warning icon in the list of installed packages:
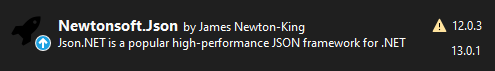
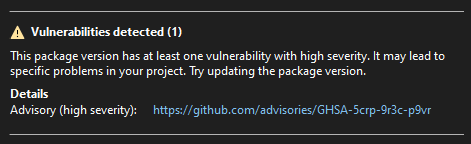
When you select the package in the list, the details pane on the right provides more information, including a link to the advisory page for the vulnerability:
If you are not using Visual Studio 2022, you can also get a list of vulnerable NuGet packages in your project or solution by using .NET CLI:
dotnet list package --vulnerable
You can see the severity of the vulnerability directly in the list, along with the link to the advisory page:
Project `FitbitWeightImporter` has the following vulnerable packages
[netcoreapp3.1]:
Top-level Package Requested Resolved Severity Advisory URL
> Newtonsoft.Json 12.0.3 12.0.3 High https://github.com/advisories/GHSA-5crp-9r3c-p9vr
While it's nice to have an option to explicitly check your project for vulnerabilities, you should automate the process to be notified of new vulnerabilities without having to do it manually, either as part of your CI build or ideally periodically, even if you are not building the project because you are not actively working on it.
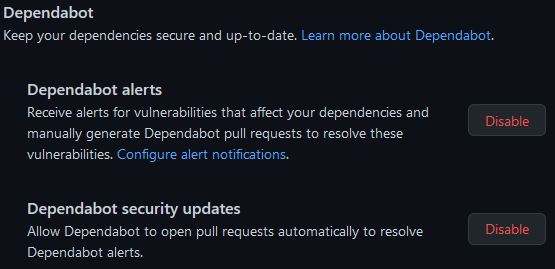
If your code is in a GitHub repository, Dependabot can do this for you. Vulnerability warnings are enabled by default for public repositories, but you can also enable them for private repositories in the repository settings:
If you host your code elsewhere, you can still use Dependabot, but you have to integrate it into your build server yourself. There is a reference repository to help you get started. Before you do that, you should check if there is already a custom integration for your build server. For example, with Azure Pipelines, you can use the Dependabot Azure DevOps Extension.
It's always a good idea to make sure you are not referencing packages with known vulnerabilities in your project. You can check this manually in Visual Studio 2022 NuGet Package Manager or with .NET CLI. It is even better if you automate the check by integrating Dependabot into your CI server.
